
Cybersecurity Basic for the Crypto Currency Investors
Reality with regards to cryptographic money exchanging is that it isn’t the make easy money course that numerous unpracticed individuals trust and trust it to
We are creative, ambitious and ready for challenges! Hire Us
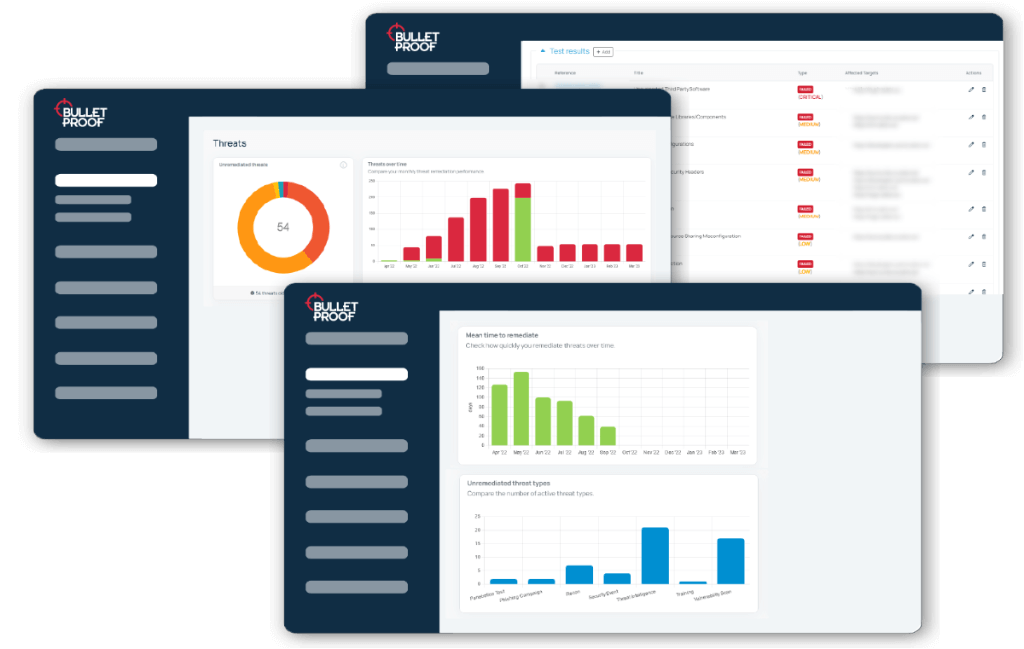
Reduce business risk with enterprise penetration testing. Effortlessly manage multiple tests, automatically prioritise findings, and meet compliance requirements, including ISO, PCI, SOC 2, & GDPR.

Leading UK CREST pen test company with 7+ years' experience & certified global pen test teams
Everything tested, including infrastructure, web & mobile apps, cloud, IoT, OT, build reviews & more
Remediation advice is given for each threat, with automatic prioritisation & tracking in our SaaS portal
Easier scoping, management & reporting of multiple tests with our dashboard-driven platform

Penetration testing at the scale of enterprise organisations comes with additional challenges. In addition to ensuring quality tests from a trusted provider, enterprises require a planned approach and a pen testing service that can cater for managing multiple test regimes. The wider nature of an enterprise’s attack surface, with challenges of legacy and shadow IT, means that a pen test provider must provide accurate scoping to get meaningful test outcomes.
There are also many different drivers for an enterprise’s full-stack pen testing needs, including DevSecOps, CISO, GRC, product owners and more. Where in-house testing teams exist, internal tests may not be as thorough or unbiased as external penetration testing from a trusted provider, and compliance requirements often demand third-party penetration testing.
CyberPentesting’s enterprise penetration testing meets all these challenges head-on to deliver a service that makes it easy to manage multiple tests and get the best outcomes.
Helps with PCI DSS, ISO 27001, GDPR & SOC 2 compliance
Complement & supplement your existing testing teams
Easily manage multiple pen test engagements with CyberPentesting
Data-driven dashboards makes it easy to engage stakeholders
Fix the issues that matter most with automatic prioritisation
Speed up remediation activities with included built-in remediation advice
A penetration test is only as good as the reporting it provides, which is why key component of CyberPentesting’s enterprise pen testing is our SaaS threat management platform. It features automatic prioritisation of uncovered threats and includes remediation advice for each and every finding. This enables enterprises to spend their limited remediation budget with surgical precision, taking risk-based decisions to get maximum security for maximum efficiency.
The platform aggregates and prioritises threats from other security services, including managed SIEM, phishing campaigns and vulnerability scanning. This gives an all-in-one view of your security posture like never before, enabling even more accurate remediation and efficient use of your budget.
Whether you’re looking for one-off pen tests for external assurance or on-going testing as part of a wider enterprise initiative, CyberPentesting provide the full range of penetration testing services.

As one of the largest UK providers of penetration testing services, CyberPentesting believe you should expect more from your penetration testing company than just a list of vulnerabilities. That’s why we give you actionable intel to power faster, more effective remediations.
Get ahead of vulnerabilities with penetration testing and on-going vulnerability scanning
Full-scale multi-site red team, black team, purple team, plus phishing & OSINT assessments
Actionable remediation advice included with each threat for faster remediation
Configure tests to meet specific compliance requirements
Grow your reputation as a responsible & secure business
Enterprise penetration testing, commonly just called pen testing, is an ethical simulated cyber attack on an enterprise’s IT & OT infrastructure. The goal is to enumerate security weaknesses, so that cyber vulnerabilities can be codified, prioritised, and remediated. The methods and tools of enterprise penetration testing vary with on what’s being tested and the scope of the test. Networks, systems, web apps, mobile apps, cloud environments, build images, IoT/OT and humans all present security vulnerabilities to enterprises.
Enterprise organisations undertaking penetration testing often have different operational and security objectives compared to SMEs and startups. Whereas an SME might say ‘test everything’ and undertake pen testing once a year, an enterprise will have separate pentesting programmes for different infrastructure components and business units. Enterprise pen testing providers will be able to facilitate this kind of multi-testing approach, and also be able to work with an enterprise’s internal pentesting teams.
Penetration testing from a reputable pen test service provider is required or recommended by a wide range of compliance standards and certifications. Bulletproof’s enterprise penetration testing can help enterprise organisations meet and maintain compliance with:
Bulletproof’s global teams of experienced pen testers use a variety of off-the-shelf and custom tools in their pentesting activities. For example, automated security scanning, custom-crafted scripts, commercial tools and hand-tailored exploits all combine with a pen tester’s insight and expertise to compromise your cyber defences. Our CREST certified penetration testers always use the right tooling for the task, using different tools and tech for asset enumeration, network discovery, attack surface mapping, exploitation, and so on.
Bulletproof’s dashboard-driven SaaS platform makes it easy to see at-a-glance prioritisation of your pen test findings, giving enterprises intel on what you need to fix first. With limited remediation budgets, the threat management feature of the portal helps enterprises get maximum impact from their remediation efforts. Threats from other services, such as managed SIEM are also displayed here, giving a powerful single pane of glass overview of your security posture.
Even in the enterprise landscape, there still exists confusion about which tool is best for your organisation: penetration testing or vulnerability scanning. This quick ‘cyber security 101’ video can help you understand the difference.

Get a fast quote for enterprise penetration testing
While the penetration testing exact methodology will depend on the type and nature of test, most penetration testing services follow the same high-level methodology. Learn more about the fundamentals of penetration testing, plus tips for how to get a good outcome, download our free Essential Guide to Penetration Testing White Paper.
Based on your defined goals, we’ll work with you to develop a tailored testing strategy.
In this reconnaissance stage, our experts use the latest groundbreaking techniques to gather as much security information as possible.
Using the latest tools and sector knowledge, we’ll uncover what’s making your critical assets vulnerable and at risk from attack.
Using a range of custom-made exploits and existing software, our penetration testers will test all core infrastructure and components without disrupting your business.
The team will determine the risks and pivot to other systems and networks if within the scope of the test. All compromised systems will be thoroughly cleaned of any scripts.
Our security team will produce a comprehensive report with their findings. You’ll have the opportunity to ask questions and request further information on key aspects of your test.
New threats are discovered every day, so CyberPentesting includes automated security scans to help you keep on top of new security weaknesses.

Reality with regards to cryptographic money exchanging is that it isn’t the make easy money course that numerous unpracticed individuals trust and trust it to

Cloud Security Position The board (CSPM) implies the procedures, instruments, and practices expected to stay aware of the security position of cloud conditions. As affiliations

Online protection has developed alongside innovation and data frameworks to turn into a pivotal part of the contemporary world. In any case, the advancement of
CyberPentesting takes pride in building and nurturing the best cyber talent to ensure our penetration testing services always get the best security outcomes for our clients. Our global teams of OSCP & CREST penetration testers are highly skilled, speak at security events and have discovered CVEs.

I take pride knowing that my team are always thinking creatively to get the best outcomes for our pentest customers. They think like the attacker and are always improving their knowledge to stay on top of emerging threats.
ASif tourab Tweet




We’ve always been very impressed with the cyber security services CyberPentesting provide us. Their professional approach, knowledge and flexibility have ensured they have become a key trusted partner in our supply chain.
asif tourab Tweet
Stay ahead of the hackers with penetration testing services to protect your systems, networks, apps & more.

Reality with regards to cryptographic money exchanging is that it isn’t the make easy money course that numerous unpracticed individuals trust and trust it to

Cloud Security Position The board (CSPM) implies the procedures, instruments, and practices expected to stay aware of the security position of cloud conditions. As affiliations

Online protection has developed alongside innovation and data frameworks to turn into a pivotal part of the contemporary world. In any case, the advancement of




