
Cybersecurity Basic for the Crypto Currency Investors
Reality with regards to cryptographic money exchanging is that it isn’t the make easy money course that numerous unpracticed individuals trust and trust it to
We are creative, ambitious and ready for challenges! Hire Us
Comprehensive network penetration tests from our certified security experts.

Internal and external network security testing gives you complete visibility over your infrastructure.
Discover new security flaws and protect your business 24/7 with automated scans for continuous security.
Pen test teams are qualified by industry recognised certification bodies, including CREST
Our simple to use dashboard prioritises test results and gives you key remediation guidance
Network or infrastructure penetration testing is a hands-on ethical hacking and network defense assessment that evaluates the security of your business network and system infrastructure. It tests internal and external networks, analysing infrastructure security for misconfigurations and design flaws, and to assess the effectiveness of network security controls.
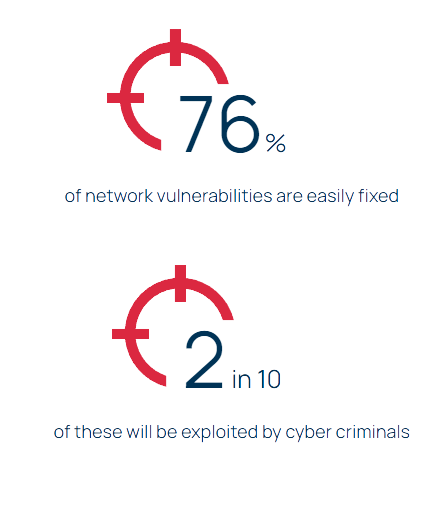
Network penetration testing services assess vulnerabilities and technical misconfigurations within a controlled environment to attempt to exploit weaknesses and offer remediation advice for strengthening network security.


Network penetration tests are carried out with an authorised simulated attack on your network to identify vulnerabilities and assess the effectiveness of security controls. The goal of network pen testing is to help you find and prioritise your security flaws before they’re discovered and exploited by a cyber criminal.
CyberPentesting’s CREST-certified penetration testers use the same tactics, techniques and procedures as real-world hackers to simulate a breach in a controlled testing environment. Penetration tests are in high demand from business of all sizes and sectors and form the basis of any cyber security strategy.
Compromised data and systems damaged from a cyber attack can quickly lead to financial and reputational damage that’s often hard to recover from. Exploiting vulnerabilities in a controlled environment through CREST-certified network and infrastructure pen testing allows you to see where your security defences are failing and helps you prioritise improvements.
We know the threat landscape is dynamic and constantly evolving which is why we offer 12-months of free vulnerability scanning with every penetration test package.

External and internal network penetration testing provide two different models of what an attacker could damage within your network. CyberPentesting recommends a blended test with elements of internal and external network security testing.
Internal network penetration testing can assess your more vulnerable internal network infrastructure. It’s usually a more in-depth test that models what an attacker could achieve if they were to get direct access to your internal network.
External network penetration testing determines how easily your system can be breached with little to no information provided up-front. Penetration testers start without any user privileges to internal systems.
CyberPentesting penetration testers are all experienced ethical hackers with a wide knowledge of different network and infrastructure technologies. They use their insight and ingenuity to discover security flaws in your organisation. Here are the Top 10 most common internal & external network vulnerabilities we find:
CyberPentesting follows industry standard best practices for our penetration testing methodology
Based on your defined goals, we’ll work with you to develop a tailored testing strategy.
In this reconnaissance stage, our experts use the latest groundbreaking techniques to gather as much security information as possible about the network and infrastructure in the scope.
This is where our network penetration testers get testing. Using the latest tools and sector knowledge, we’ll uncover what’s making your critical assets vulnerable and at risk from attack.
Using a range of custom-made exploits and existing software, our network penetration testers will test all external and internal-facing systems without disrupting your business.
The team will determine the value of the compromised targets by trying to elevate privileges and pivot to other systems and networks if you are looking to understand the full impact of the threat. All compromised systems will be thoroughly cleaned of any scripts.
Our security team will produce a comprehensive report with their findings. Once received, we’ll invite you for a collaborative read through. You’ll have the opportunity to ask questions and request further information on key aspects of your test.


If you’re interested in our penetration testing services, get a free, no obligation quote today by filling out the form below.
After our team of experts has completed network penetration testing, you will receive a comprehensive report in our modern dashboard-driven portal. As well as prioritising the discovered threats, we include key remediation advice to help speed up your remediation efforts.
Our network pen test reports include:
All testing scopes are specific to your organisation so please use the above as a guide.
All tests are tailored to you so use this as a guide.
Testing can be performed against a non-production replica of your live environment, such as a UAT/QA environment, to ensure no risk to your live services. If testing against production is unavoidable, we can coordinate our testing activities to minimise the impact. You can also specify things like no denial of service (DoS), meaning tests will have a negligible impact on your day-to-day operations.
Whilst we do not offer free retesting, we do offer 12-month vulnerability scanning.
Standard best practices recommend regular cyber security assessments and penetration tests are a key part of this. The ramifications of security breaches can result in severe financial and reputational losses. Our network pen testing experts will identify the risks posed to your business and the report helps create a comprehensive plan to strengthen your cyber resilience. In as little as 3 days (depending on scope) and with minimal disruption to your business, you’ll know how to stay ahead of the hackers.

Reality with regards to cryptographic money exchanging is that it isn’t the make easy money course that numerous unpracticed individuals trust and trust it to

Cloud Security Position The board (CSPM) implies the procedures, instruments, and practices expected to stay aware of the security position of cloud conditions. As affiliations

Online protection has developed alongside innovation and data frameworks to turn into a pivotal part of the contemporary world. In any case, the advancement of




