
Cybersecurity Basic for the Crypto Currency Investors
Reality with regards to cryptographic money exchanging is that it isn’t the make easy money course that numerous unpracticed individuals trust and trust it to
We are creative, ambitious and ready for challenges! Hire Us
Ennhance your cybersecurity effectiveness

Get Cyber Security Consulting Service
Cybersecurity has now become the boardroom conversation and a top leadership concern.
Cybersecurity is often seen as complex. As the threat landscape is quickly evolving, organizations need to keep up pace with the newer cyberattacks methods and know if their cybersecurity capabilities can answer and recover from these threats. To implement a secure environment, a strong cybersecurity program built around people, processes and technology is required.
Cybersecurity consulting capabilities can support organizations in their daily commitment to a successful cybersecurity program.
95%
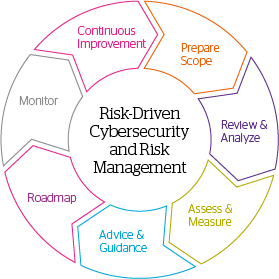
CyberPentesting provides a comprehensive set of cybersecurity services that enhance cybersecurity effectiveness and delivers awareness that qualifies investment to protect critical assets.
CyberPentesting global capabilities, breadth of expertise, service and focus across various major industry, deep pool of talent leveraged through strong partnerships and alliances are the CyberPentesting key differentiators. Building the firm of the future, our robust corporate governance and focus on sustainability matters position us as your trusted partner for IT excellence.
CyberPentesting Cybersecurity services will help you drive informed security decisions that protect valuable assets, to provide situational awareness, and justify the ROI on the security spend.

Readiness
Are your cybersecurity investments effective and do you know how secure are your defenses?
PCI readiness assessment
Support to the organization through the necessary activities to understand and attest to their Cardholder Data Environment (CDE).
Business impact analysis and continuity planning
Organizational risk assessment to highlight critical and time-sensitive business functions, current state readiness and plan of action for a BCP to offset risk and minimize loss and business disruption.
Security/incident response capabilities
Enhanced Cyber Incident Response (IR) Capabilities by analyzing existing cyber IR capabilities and providing recommendations for enhancement to improve incident response.
Executive engagement and training
Platform for senior leadership and management, to review, learn, understand the cybersecurity threats, trends, patterns, business disruptions and potential financial, brand reputational impacts.
Anti-phishing security
Enterprise security awareness services to assess and practice understanding and reaction to enterprise threats from social engineering attacks and guidance to defend organizations’ resources, assets, and investments from such threats – and elevate the effectiveness of the security awareness across the enterprise.

Program
Data governance services
Data classification (based upon sensitivity) process and insight to where the data is being stored.
Information security (InfoSec)
Resources (full time equivalent) to design, implement and / or manage a security risk management program.
Enterprise governance, risk canagement and Compliance
Comprehensive solutions that catalog, monitor, update, notify, and manage a company’s operational GRC needs.
Security policies and standards enhancement
Establishment and integration of a control framework for external security and privacy requirements, in addition to the definition of processes to support management, monitoring, and reporting of defined regulatory, industry and international requirements.
Cybersecurity risk management capability
Review and update of the risk register, identification of risk acceptation & paths of risk escalation, as well as a review of the risk appetite matrix.

Assessment
Cybersecurity capabilities assessment
Comprehensive review of all aspects of an organization’s cybersecurity posture and communication of the state of security that key stakeholders can utilize to strategize and prioritize organizational cybersecurity needs.
Cloud security assessment
Assessment of the security and risk posture of public clouds in use by clients.
Penetration testing
Management compliance verification of existing defenses against vulnerabilities and measures the effectiveness of security in-place.
Third party management services
Identification of third party’s role, access requirements and data interaction, as well as the risk assessment of high-risk third parties.

Guidance
Security governance and organization update
Review of existing governance models, structure and process, in addition to the definition of a gap analysis and governance operating model to identify structure inconsistencies among governance mechanisms.
Chief Information Security Officer (CISO) as a Service
Virtual or on-site senior security practitioner to serve as the Chief Information Security Office (or like role) responsible to the organization for the management (establishing, implementing and/or maintaining) the appropriate security hygiene to defend company data.
Data flow mapping, threat modeling and reference architecture
Analytical review of applications, systems, or environments via detailed Threat Modeling methodology, documentation of Data Flows and Reference Architectures that minimize threats by limiting threats by examination.
Disaster response planning and preparation
Comprehensive assessment of the organization’s disaster planning strategy and its ability to respond and recover.
We put ourselves in our clients’ position
We look to work with your organization as equal partners in this journey.
We adapt to the business culture of our clients
We never impose a “one size fits all” approach. The approach in utilized for your organization will be specifically tailored for your organizations’ specific needs.
We address your business needs with flexibility while incorporating tried and tested tools
We help deliver a customized service for our clients while being cost-effective.
We provide outstanding value for our clients’ spend & highest quality output
We believe that quality should drive the decisions not cost. We strive to provide robust service with no compromise in quality and optimize spend.

Reality with regards to cryptographic money exchanging is that it isn’t the make easy money course that numerous unpracticed individuals trust and trust it to

Cloud Security Position The board (CSPM) implies the procedures, instruments, and practices expected to stay aware of the security position of cloud conditions. As affiliations

Online protection has developed alongside innovation and data frameworks to turn into a pivotal part of the contemporary world. In any case, the advancement of