
Cybersecurity Basic for the Crypto Currency Investors
Reality with regards to cryptographic money exchanging is that it isn’t the make easy money course that numerous unpracticed individuals trust and trust it to
We are creative, ambitious and ready for challenges! Hire Us
Speed up your remediations with network, web app, mobile & cloud pen testing from a UK CREST penetration testing company. Pen tests help with compliance, including ISO, PCI DSS, SOC 2 & more.

Protect your business 24/7 with automated scans included with every penetration test
CyberPentesting prices are highly competitive without sacrificing quality, keeping you protected
Pen test teams are qualified by industry recognised certification bodies, including CREST
Our simple to use dashboard prioritises test results and gives you key remediation guidance

Penetration testing, also known as pentesting or ethical hacking, is where a pen testing company attempts to access and compromise your network, system and application security. By simulating the actions of a real-world attacker in a controlled environment, pen testing provides a list of your security weaknesses. The goal of penetration testing is to help you fix your vulnerabilities before they’re exploited by a cyber criminal. Penetration testing services from a reputable pen test provider is widely considered standard best practice, and pen testing should be a foundational component of your risk management programme. Penetration tests are also required for many certification standards, including PCI DSS, SOC2, ISO 27001 & more.
Penetration testing uses human skill & insight to uncover threats
Continuously uncover the latest security threats to your business
Results delivered in a modern dashboard-driven platform
Fix issues fast with remediation advice included with each threat
Give customer confidence that you take their security seriously
Meet ISO 27001, PCI DSS, GDPR, SOC2 requirements & more
We offer a variety of pen tests which can be delivered as one-offs to spot check your security, or on a recurring basis as part of an on-going security strategy. The exact type of penetration test you require will depend on your security objectives and compliance needs, and we may recommend combined testing – such as a mix of web application and infrastructure testing – to ensure we meet your goals.

Penetration testing services are widely recognised as the best way to stay on top of evolving cyber threats and prevent data breaches. It’s recommended to perform a pen test at least once a year, and on significant change to your infrastructure.
Given its position as an essential best practice, penetration testing is either recommended or required for a wide range of information security and cyber security standards. Using a reputable pen test service provider will directly help your business meet compliance with:

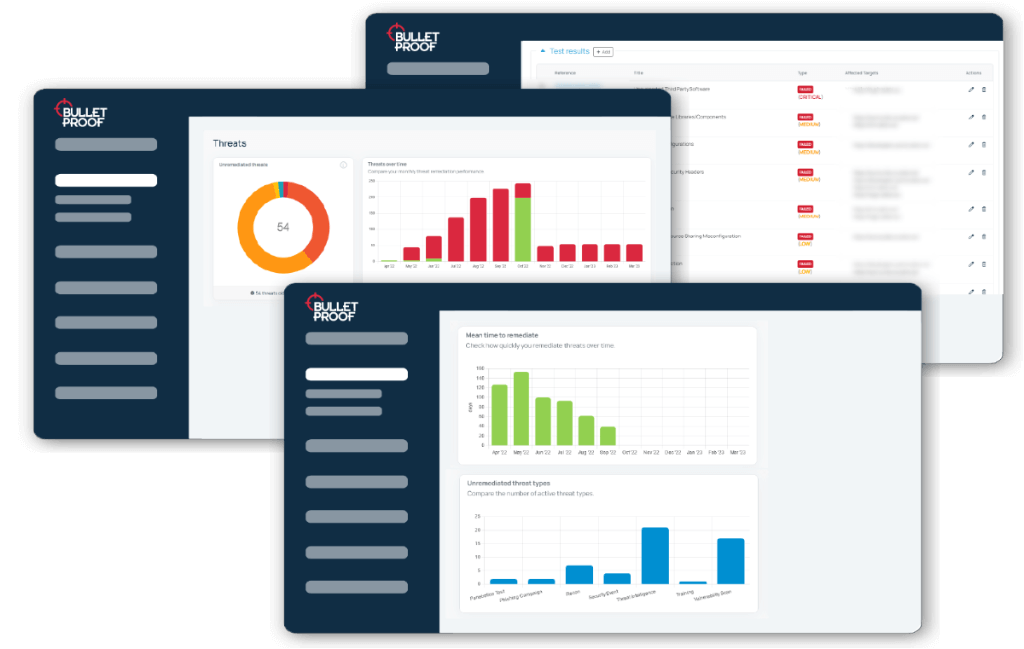
Expect more from your penetration testing company than just a list of vulnerabilities. As one of the leading UK security testing companies, CyberPentesting gives you actionable intel to power faster, more effective remediations.
A penetration test, often called a pen test or pentest, is a methodical simulated attack on your IT infrastructure, with the aim of discovering security vulnerabilities. The methods and tools of the security testing vary depending on what’s being tested, such as network, systems, web apps, mobile apps or the cloud. Pen testing is requirement of many compliance standards, including PCI DSS, ISO, SOC 2, HIPAA, FTC & more.
As a trusted penetration testing service provider, Bulletproof offers a variety of pen tests, as one-offs to spot check your security or on a recurring basis as part of an on-going security strategy. The exact type of penetration test you require depends on your security objectives and compliance needs, such as PCI DSS pen testing. We often find that combined testing – such as a mix of web application and infrastructure/network security testing – gets the best outcome.
Vulnerability scanning, sometimes called automated penetration testing, uses scanning software to methodically and simply scan for a list of known vulnerabilities. Penetration testing on the other hand uses in depth analysis and human ingenuity to uncover security flaws that can’t be found by vulnerability scanning alone.
Automated testing and vulnerability scanning are an important part of your defences, such as helping regular patching, whereas a penetration test provides detailed reporting and remediation advice from cyber security experts. Penetration testing companies will use both tools in their arsenal to make sure your business is protected against cyber threats.
Bulletproof’s seasoned pen testers use a variety of commercial and bespoke tools to help their pentesting activities. This includes automated security scanning, custom scripts and tailored exploits to compromise your cyber defences. Our CREST certified penetration testers always use the right tool for the job, using different tooling and technology for asset enumeration, network discovery, attack surface mapping, exploitation and more. Automated tooling is a key weapon in our pen tester’s arsenal, but automated scans alone are not the same as a true penetration test.
Penetration testing projects vary in length and complexity depending on a number of factors, including what apps and infrastructure are being tested, the aims of the test, and the testing parameters. As a leading UK penetration testing service provider, we take the time to understand your aims and objectives, so we can scope a best-fit security test that delivers value for money. As a specialist penetration testing company, we have dedicated pentest scoping experts to help you get the best outcome for your pen test.
Pentesting engagements vary in their duration depending on the scope of the test. There are several factors to consider, such as if the pentest is internal or external, network size and complexity, and how much information is disclosed upfront. Bulletproof’s dedicated SaaS portal powers our intelligent reporting, meaning that more time is spent delivering penetration testing services, and less time taken up by report writing. This means your business gets a better understanding of the results, and your test is more cost effective.
Best practices, compliance standards and security professionals all agree that penetration testing should be conducted at least once a year. In addition, extra pentesting should be performed upon significant change or upgrades to your infrastructure. This schedule of security testing is even mandated by certain compliance standards, including PCI DSS.
Bulletproof penetration testing is specifically designed to safely identify and exploit vulnerabilities with minimal risk of disrupting your business operations. Testing can be also performed against a non-production replica of your live environment, such as a UAT/QA environment. A common specification on testing is ‘no denial of service (DoS)’, meaning tests will have a negligible impact on your day-to-day operations.
CREST is an internationally recognised body that promotes the highest standards of security testing. Bulletproof is a member of CREST for penetration testing and security scanning, and our expert pentesters additionally individually hold CREST certifications. Selecting a CREST certified penetration testing company gives you confidence that your pen testing services will be carried out to the highest technical and ethical standards.
Bulletproof has innovated our own technology solutions so that almost all types of penetration testing can be performed remotely. Whereas other providers will insist on on-site access for their pentesters, Bulletproof can perform pen testing services remotely.
At the end of the technical operations, the lead pentester assigned to you will create the comprehensive report and make it available in the Bulletproof threat management portal. The report will detail each threat, the business impact, likelihood of exploitation, how easy it is to fix. Crucially, remediation guidance is included for each and every pen test finding, and the dashboard makes tracking remediations easy. This makes it easier and quicker to improve your security posture. A thorough debrief call is also available, depending on the scope of the test.


Reality with regards to cryptographic money exchanging is that it isn’t the make easy money course that numerous unpracticed individuals trust and trust it to

Cloud Security Position The board (CSPM) implies the procedures, instruments, and practices expected to stay aware of the security position of cloud conditions. As affiliations

Online protection has developed alongside innovation and data frameworks to turn into a pivotal part of the contemporary world. In any case, the advancement of
CyberPentesting takes pride in building and nurturing the best cyber talent to ensure our penetration testing services always get the best security outcomes for our clients. Our global teams of OSCP & CREST penetration testers are highly skilled, speak at security events and have discovered CVEs.

I take pride knowing that my team are always thinking creatively to get the best outcomes for our pentest customers. They think like the attacker and are always improving their knowledge to stay on top of emerging threats.
ASif tourab Tweet




We’ve always been very impressed with the cyber security services CyberPentesting provide us. Their professional approach, knowledge and flexibility have ensured they have become a key trusted partner in our supply chain.
asif tourab Tweet